Advanced Security Analytics ModuleNetwork security snapshot for threats and intrusion detectionAdvanced Security Analytics Module (ASAM) is a network flow based security analytics tool that helps in detecting network intrusions, using the state-of-the-art 'Continuous Stream Mining Engine™' technology, and classifying the intrusions to tackle network security threats in real time. ASAM is an add-on module with NetFlow Analyzer, therefore, does not need any additional hardware investment. The flows(NetFlow, sFlow, IPFIX, netstream etc.) are exported by the devices (routers and switches) to NetFlow Analyzer. These flows are analyzed by ASAM and the network anomalies are detected. As this is done in real time, continuous updating of the network threats keeps the enterprise network secure. Advanced Security Analytics module gives actionable intelligence (Network security views) to avert a broad spectrum of external and internal security threats. Network snapshot of ASAM displays a list of grouped threat/ anomaly as a problem and further, the problems are categorized in to three major problem classes (Bad Src-Dst, DDoS, Suspect Flows). The set of classes used for classifying problems with a brief description is given here. The security snapshot in NetFlow Analyzer shows the problem classes and problems along with the number of events occurred. ASAM also assigns severity to all the threats as Info, Warning, Major or Critical. The pie charts and line graph helps the user to grasp the network "security posture" in one glance. You can view the list of all the classes and respective problems here. Users can also select custom time period as per their requirement and filter the events based on
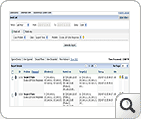
(Click on the image to enlarge) You can drilldown in to any of the problems and view the following event list :
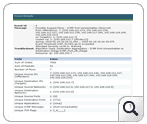
Drilling down further will give more details regarding a particular threat/event:
ASAM helps you take informed and reliable decisions on your network security! Service Pack | Download 30-day free trial | Request Demo
| |||||||||||
- 关于ManageEngine
- |
- 客户名录
- |
- 媒体资讯
- |
- Newsletter
- |
- 联系我们